Rest Api Key Authentication Example - Searching for a method to stay organized effortlessly? Explore our Rest Api Key Authentication Example, created for daily, weekly, and monthly planning. Perfect for students, experts, and hectic parents, these templates are easy to personalize and print. Remain on top of your jobs with ease!
Download your perfect schedule now and take control of your time. Whether it's work, school, or home, our templates keep you efficient and hassle-free. Start preparing today!
Rest Api Key Authentication Example

Rest Api Key Authentication Example
This 52 week Bible reading plan is your weekly guide to reading the Bible in one year The plan combines weekly scripture readings from the Old Testament and the New Testament so you can read through the entire Bible in 52 weeks Each week contains a set of seven readings Download Printable Bible in a Year Reading Plan. Skip to main content. Watch. Resources. Classroom. About. Give. Sermon on the Mount. How to Read the Bible.
Free Printable Chronological Bible Reading Plan Bible Study Printables

Most Used REST API Authentication Methods Strategies
Rest Api Key Authentication Example · You can download the free printable chronological Bible reading plan PDF by clicking on the button below. Use this PDF to check off each set of scriptures as you read the Bible chronologically. There are plenty of other Bible reading plans you can follow to read God’s Word on a preferred timetable. Choose your time frame format and the books of the Bible you want to read then print it out
January 6 Genesis 18 1 21 7 January 7 Genesis 21 8 23 20 Genesis 11 32 Genesis 24 1 67 January 8 Genesis 25 1 4 Chronicles 1 32 33 Genesis 25 5 6 12 18 Chronicles 1 28 31 34 Genesis 25 19 26 7 11 January 9 REST API Best Practices Concepts Structure And Benefits AltexSoft Available Reading Plans. Old/New Testament. Each day includes a passage from both the Old Testament and New Testament. Chronological. Read the Bible in the chronological order in which its stories and events occurred. Beginning. Read the Bible from start to finish, from Genesis to Revelation. Historical.
Download Printable Bible In A Year Reading Plan BibleProject

The REST API Implementation Flow
Daily Bible Reading Program Chronological Plan 1 Year Plan These readings are compiled according to recent historical research taking into account the order in which the recorded events actually occurred This is a fantastic plan to follow if you wish to add historical context to your reading of the Bible How To Sign And Validate JSON Web Tokens JWT Tutorial
Susan L Davis has a free printable chronological Bible reading plan available on her site It is super simple and you can print it out and keep it with your Bible study journal so you know which verse to read each day Best Practices Of API Authentication Bitbucket REST API Authentication API Token OAuth Authentication

API Key Authentication In ASP NET Core Web API Dot Net Office
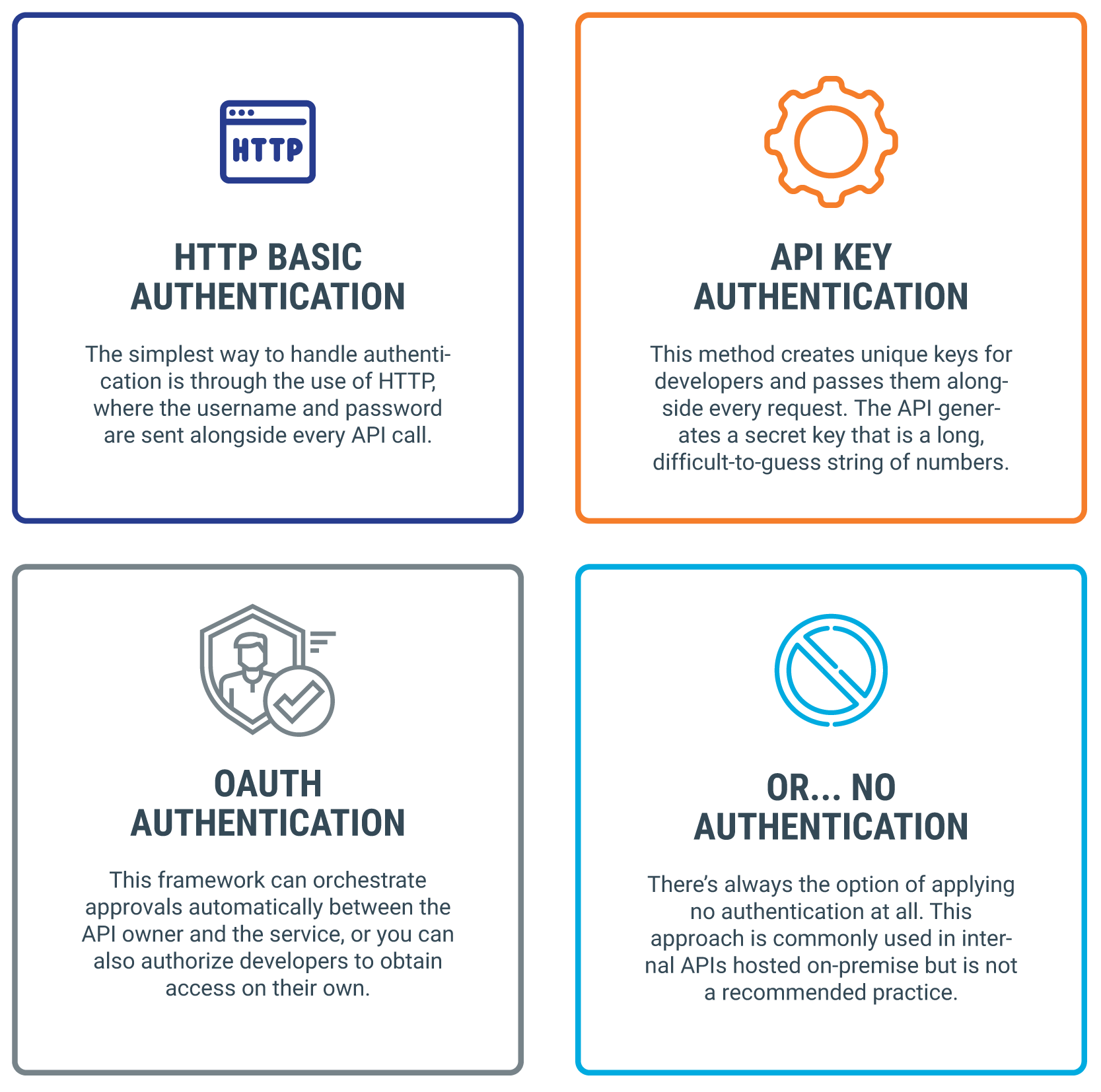
Api Authentication Methods Riset

Top 4 API Authentication Methods The Ultimate Guide
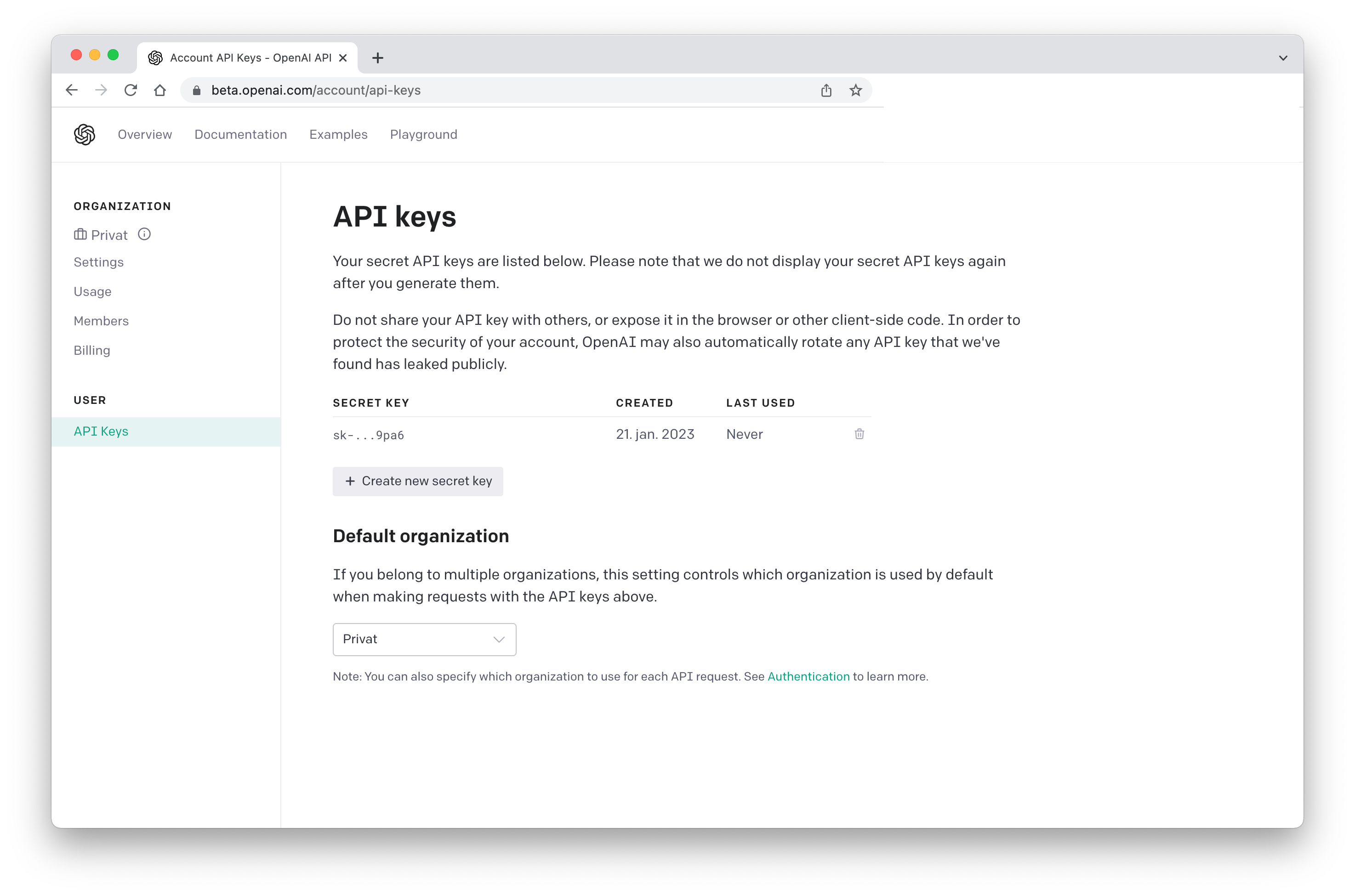
GPT 3 REST API Node js Example Like ChatGPT Easy API And Database Backend
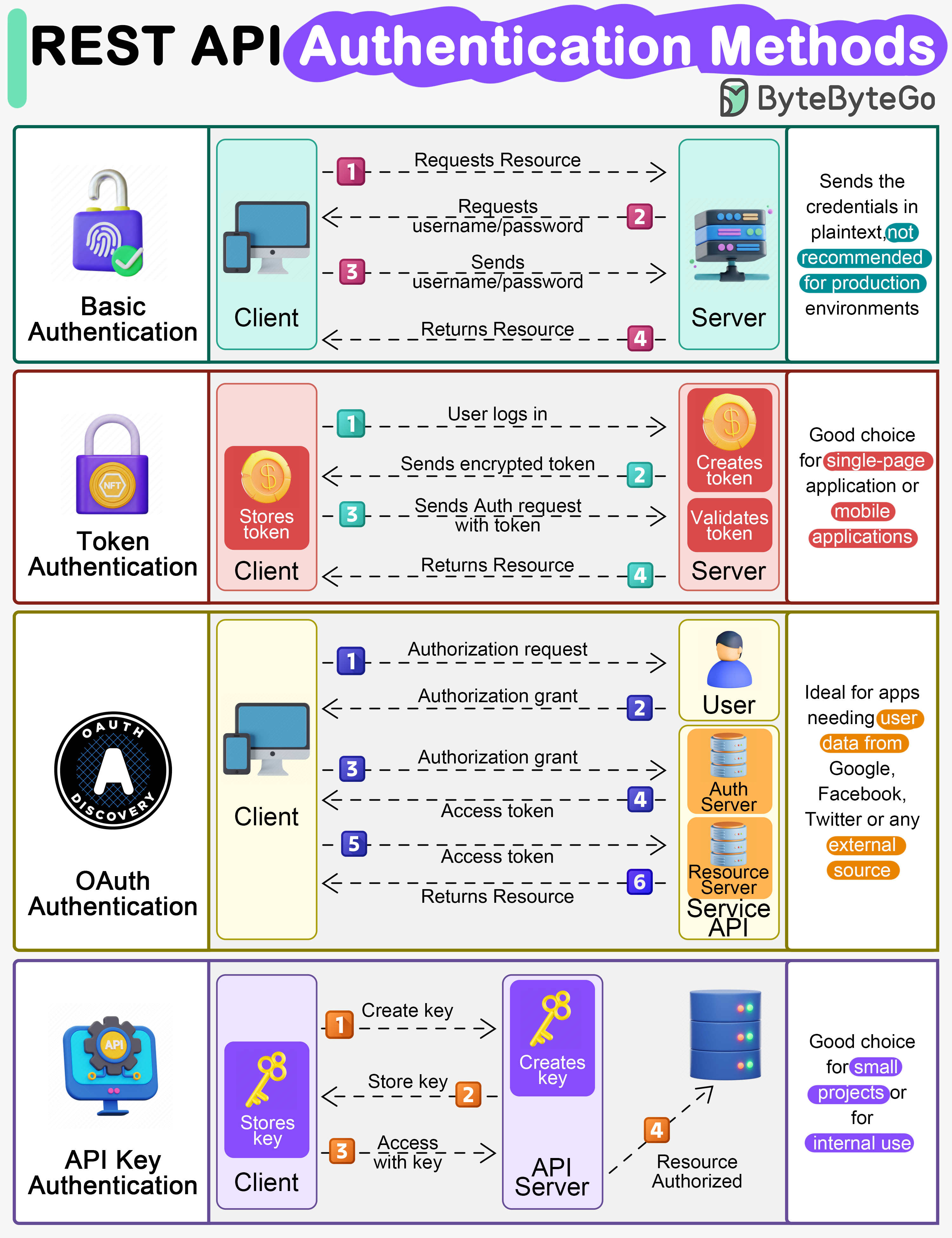
EP91 REST API Authentication Methods
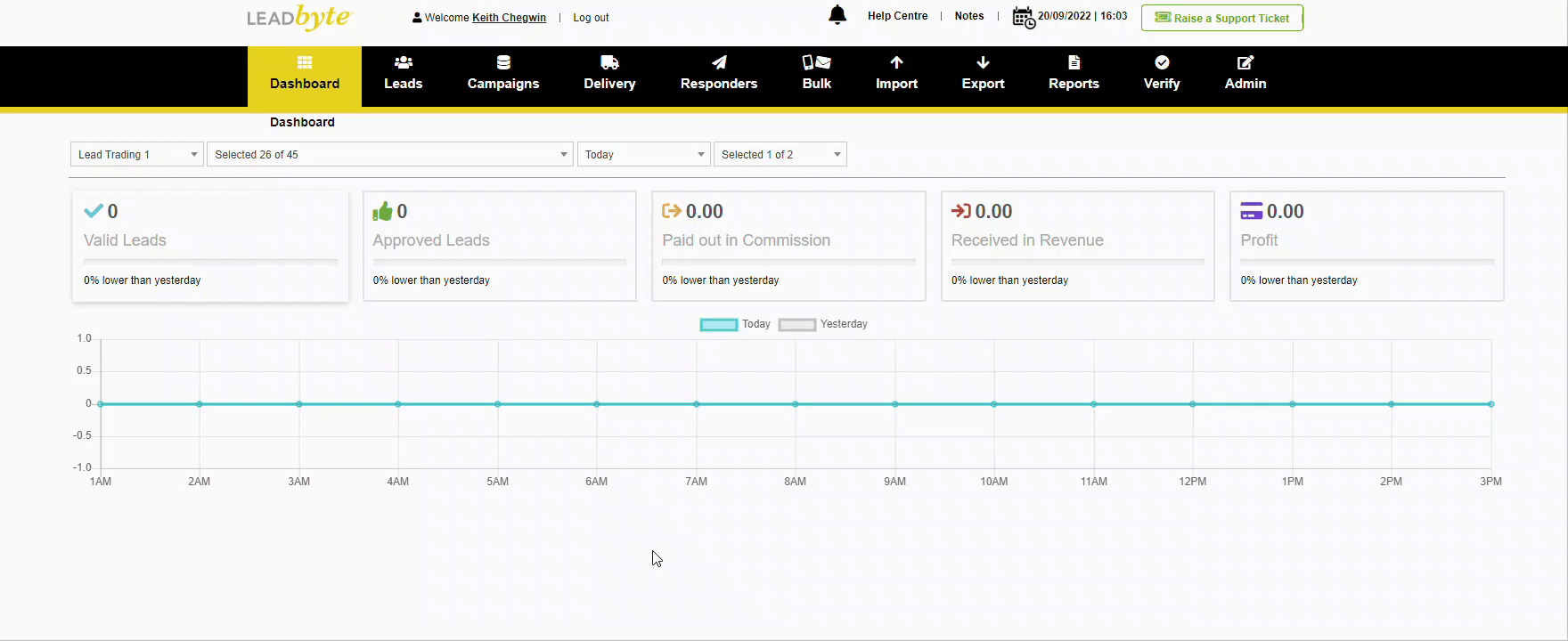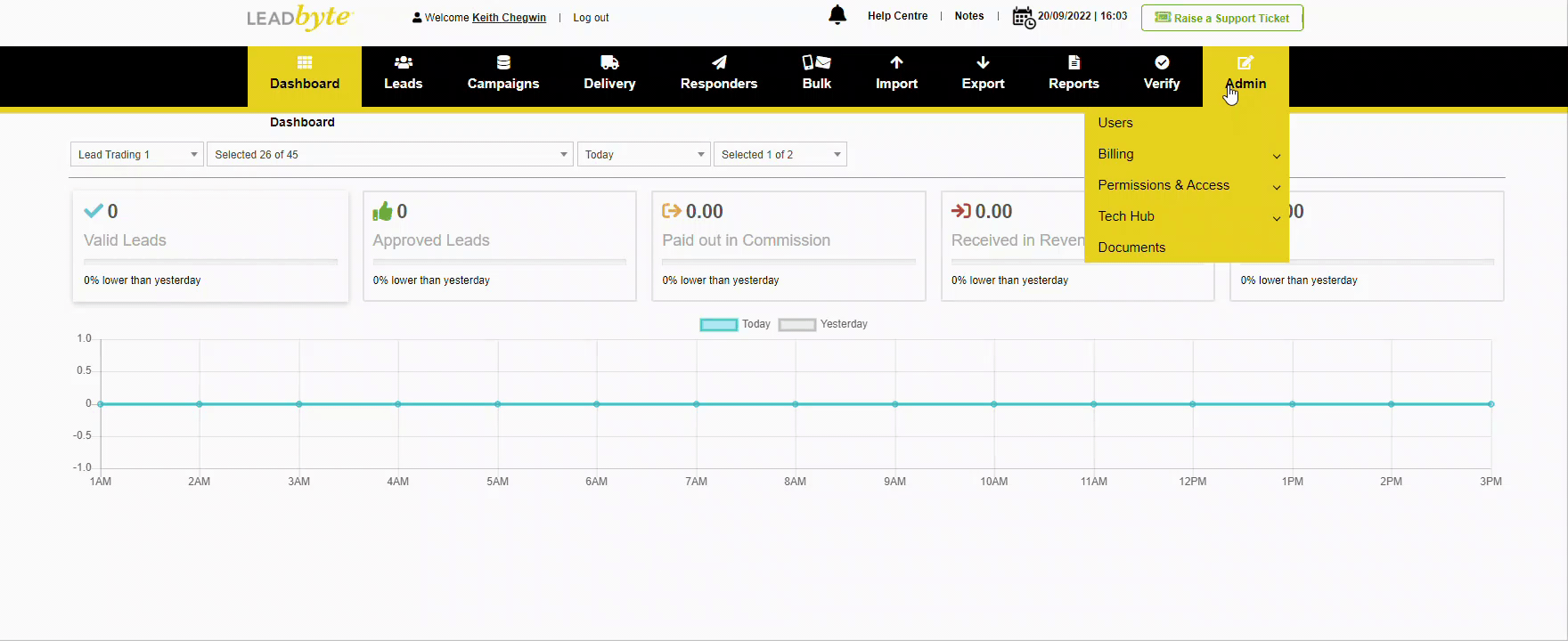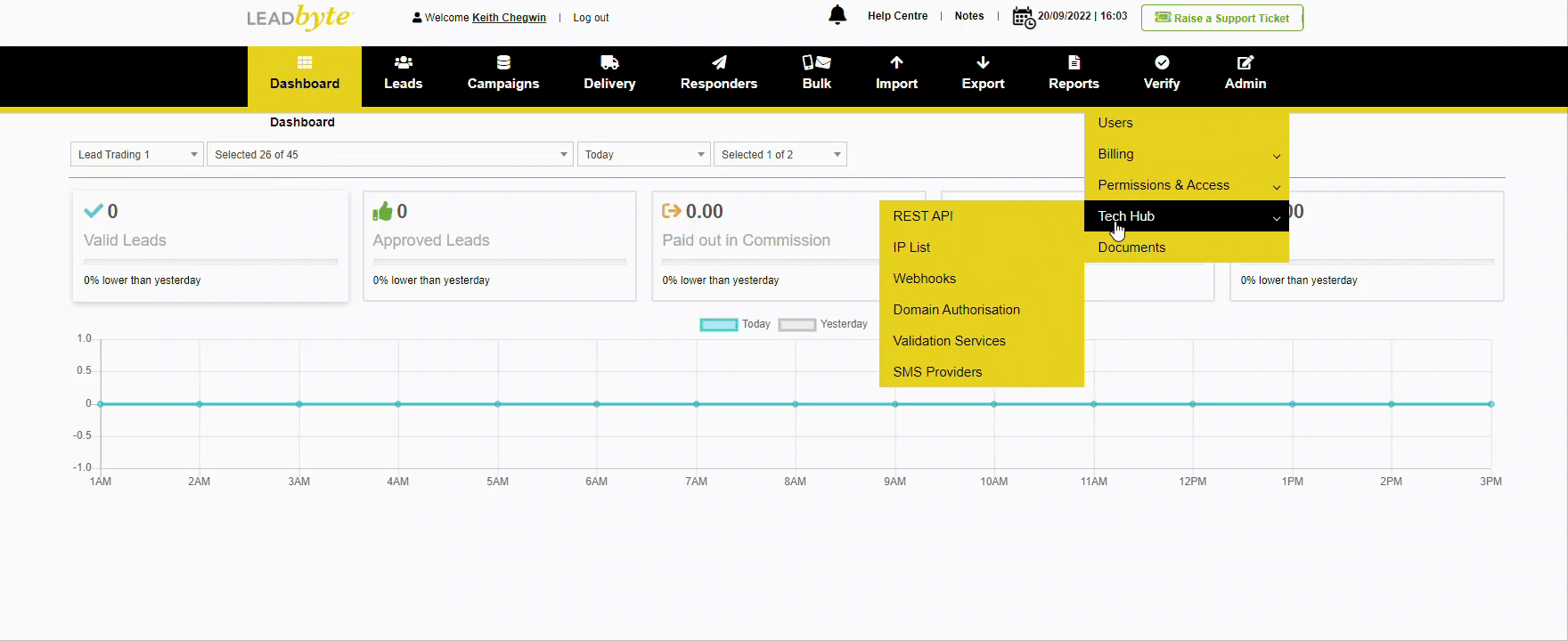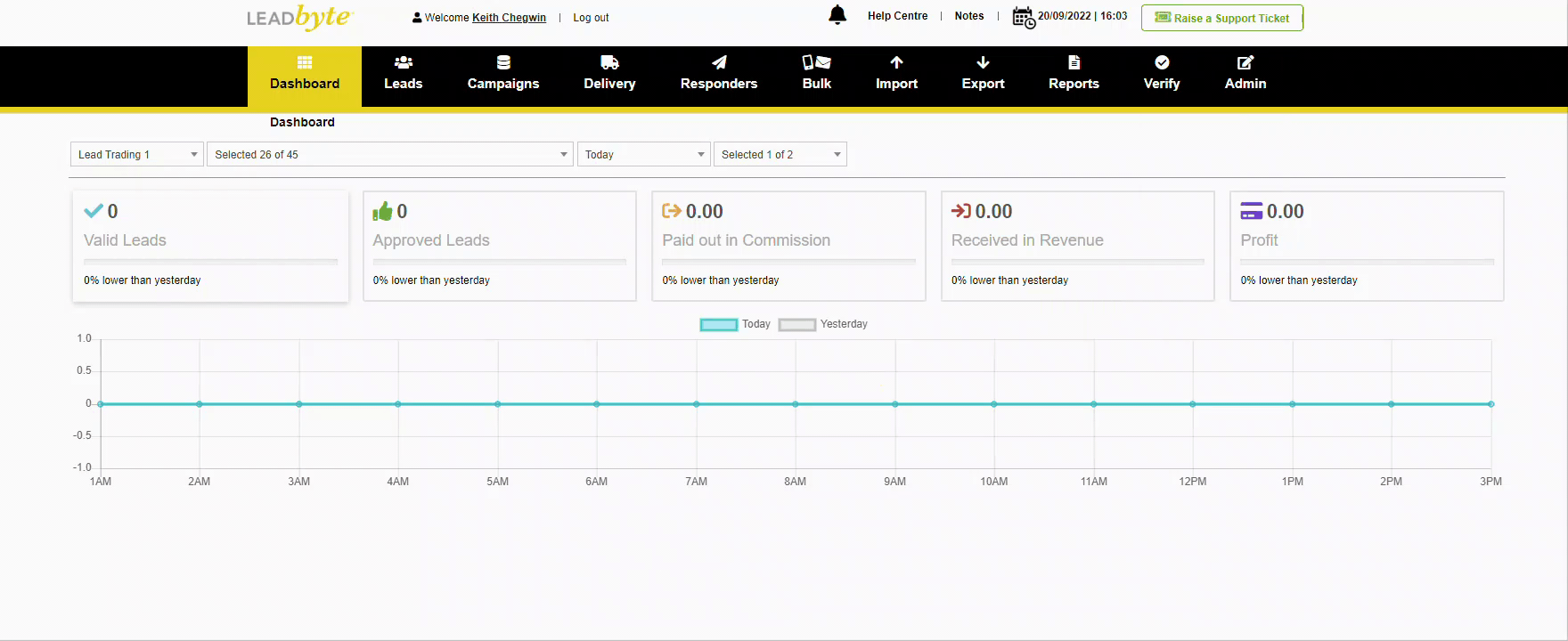
Create REST API Key LeadByte Support
Adding API Key Authentication To ASP NET Core Web API With

How To Sign And Validate JSON Web Tokens JWT Tutorial

API Key Authentication PropelAuth Blog
Common Rest Api Authentication Methods Explained Security Boulevard Riset