Ntlm Authentication Example - Searching for a method to stay organized effortlessly? Explore our Ntlm Authentication Example, designed for daily, weekly, and monthly planning. Perfect for students, professionals, and busy parents, these templates are easy to personalize and print. Remain on top of your tasks with ease!
Download your perfect schedule now and take control of your time. Whether it's work, school, or home, our templates keep you productive and stress-free. Start preparing today!
Ntlm Authentication Example

Ntlm Authentication Example
Insanity Workout Calendar MONTH 1 MONTH 2 Title insanity workout calendar Created Date 4 19 2022 11 04 22 AM 56. Fit Test & Max Interval Circuit. Max Interval Plyo. Max Cardio Conditioning & Insane Abs. Max Recovery. Max Interval Circuit. Max Interval Sport Training. Rest.
Download amp Print The Insanity Workout Calendar amp Schedule

NTLM Authentication
Ntlm Authentication Example · For those participating in the Insanity fitness program, the Insanity calendar PDF is an indispensable tool. Moreover, the calendar provides a detailed daily plan of the program’s workout routines, making it simple to keep track of progress and stay motivated. This free printable Insanity workout planner includes a section on motivation to help you when you want to quit a countdown calendar a weight loss tracker to track body measurements and weight a food diary to track calories and macros and an Insanity calendar
Click the links below to downlaod a printable version of the modern Insanity workout schedule There are two versions available for free download regular and insanity deluxe Each version is available in both Excel and PDF formats NTLM Authentication Definition Protocol Vulnerabilities Redlings The Insanity calendar is an extreme 60 day at home total body workout. Over the course of this schedule, you'll take on gruelling cardio and plyometric drills that are coupled with intervals of strength, power, resistance, and core training. Print, download or save a copy of the Insanity calendar today.
Insanity Workout Calendar ReviveLifeFitness
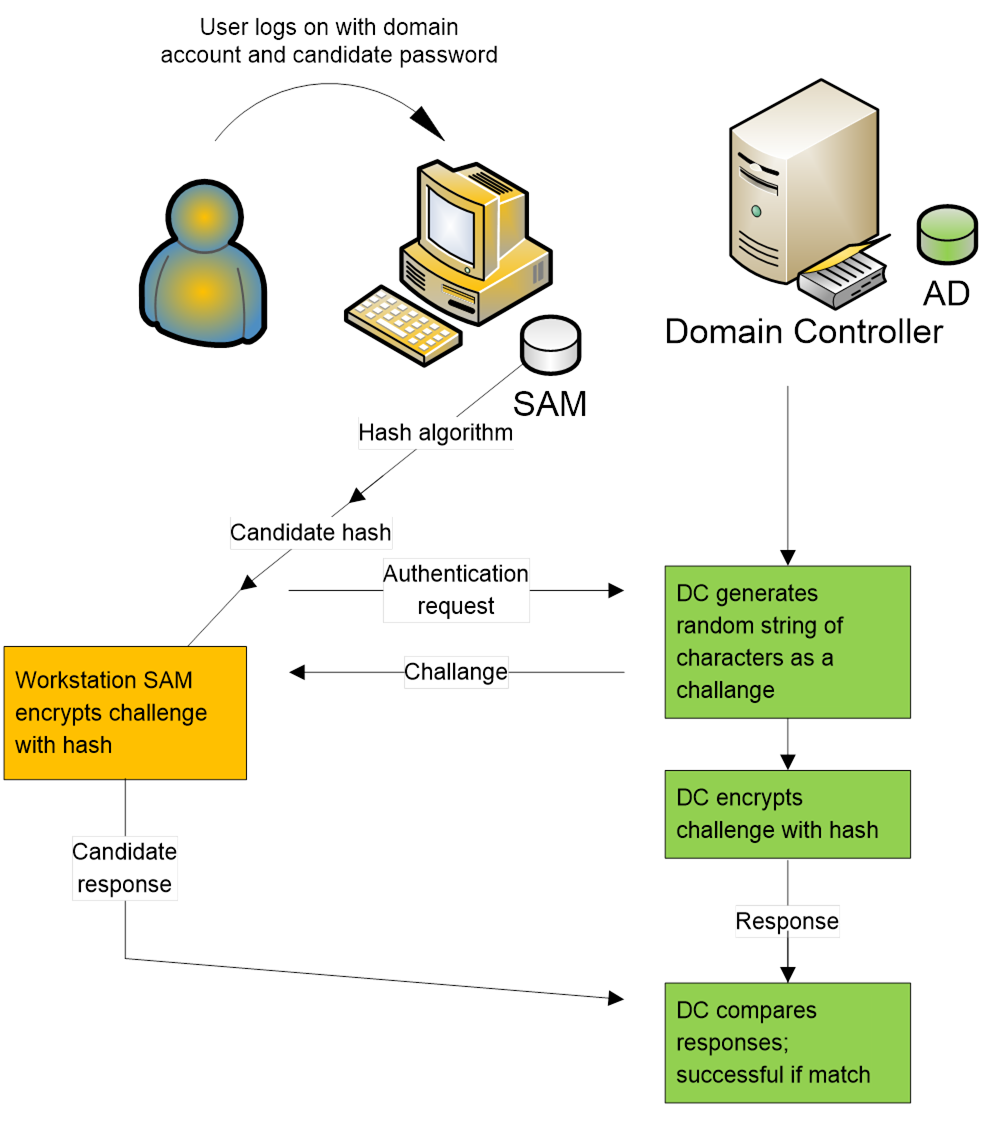
Chapter 4 Account Logon Events
CHECK A BOX EVERY DAY YOU DO YOUR INSANITY WORKOUT FIT TEST You can also find this Fit Test on the DIG DEEPER DVD Perform each of the exercises listed below for 1 minute Do as many reps as you can in 1 minute and record below Rest when needed Be sure to warm up first MONTH 1 SWITCH KICKS GLOBE JUMPS POWER Video How To Set Up Email Domain Authentication
Download Print Your Insanity Calendar Down below you have the workout schedule for the very popular home fitness program called Insanity by Beachbody The Insanity workout was first released in 2009 and its reputation as the hardest workout ever put on SMB Access Is Denied Caused By Anti NTLM Relay Protection By NTLM Authentication VREST NG Documentation
Malintha s Blog NTLM Authentication Basics
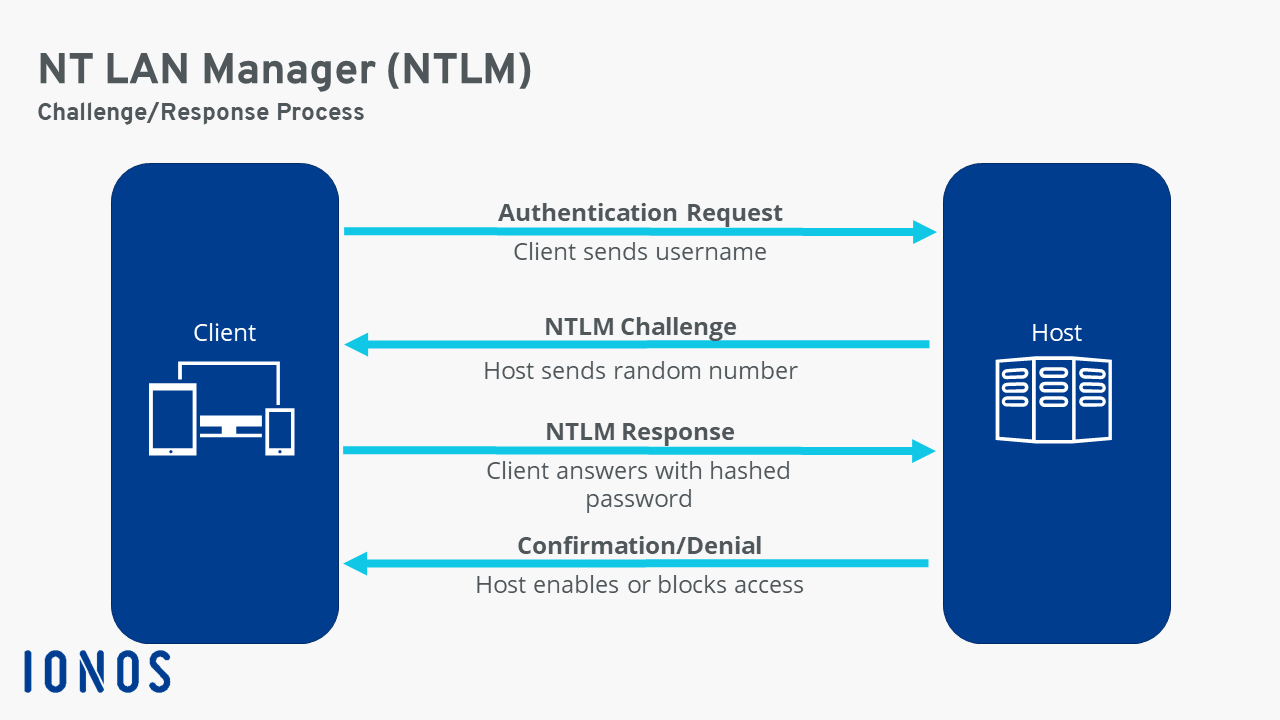
What Is The NTLM NT LAN Manager Protocol IONOS UK
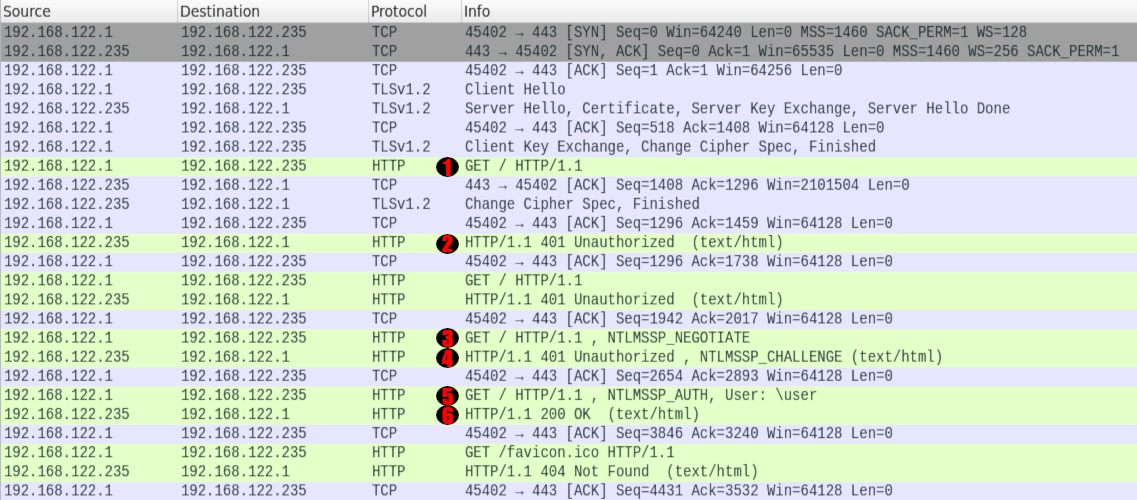
Dissecting NTLM EPA With Love Building A MitM Proxy

Unmasking The Exploitation Of NTLM Tokens In The City s Secure Network
JMeter NTLM And Basic Authentication Example How Can We Achieve NTLM
Bypassing NTLM Auth Over HTTP LeakIX Blog

How NTLM Authentication Works NTLM Hash Encryption And Decryption

Video How To Set Up Email Domain Authentication

What Exactly Is Multi factor Authentication MFA And How Does It Work
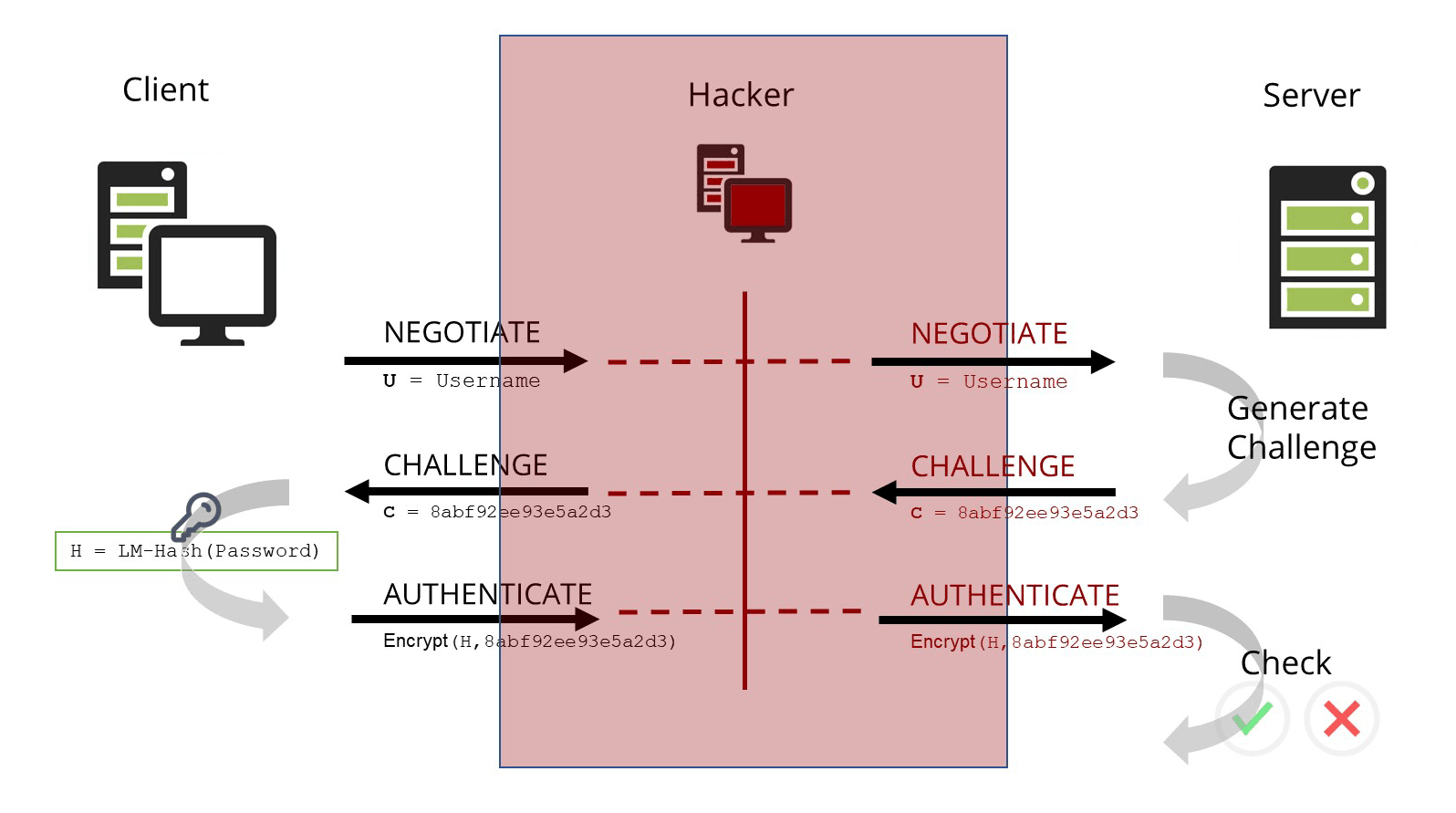
NTLM Authentication Definition Protocol Vulnerabilities Redlings